ClickFix: A New Social Engineering Threat
A new social engineering tactic known as ClickFix has emerged, posing significant risks to everyday users regardless of whether using a PC or a Mac. Though this specific lure is novel, you may already be aware of the technique, as it is similar to the Fake CAPTCHA attack we posted about in January.
In each case, the attacker needs your help. Traditional phishing and malicious web pages are easier to block. The Digital Security and Trust team and medical center counterparts do a lot to prevent these threats from reaching you. So, the attacker needs you to take extra steps to install the malware and bypass protections.
Using the Command Prompt
To fully deploy the malware, an attacker needs you to utilize your command prompt. If you aren’t used to doing this, don’t worry. You’re probably not using prompts for your regular computing. It is far more likely that an app or website has the resources that you want a simple click away. For reference, here is what a command prompt looks like on a PC:
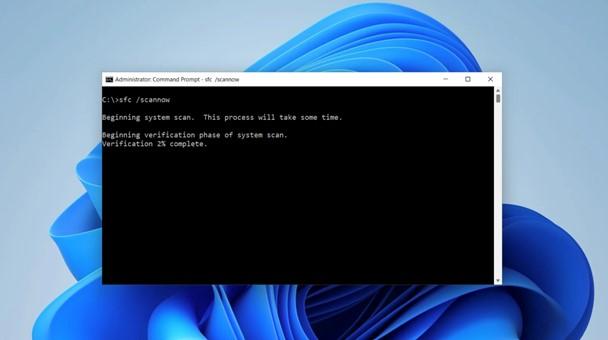
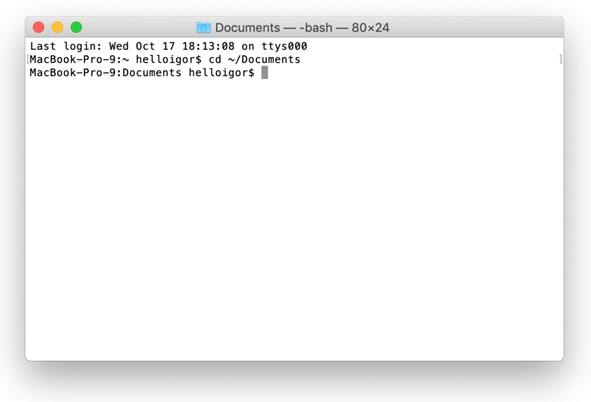
Here is what Apple’s version, the Mac Terminal, looks like:
BOTTOM LINE
DO NOT copy-paste commands of any type if you don’t normally perform this activity as part of your job. Even if you are interacting with a legitimate business or service, there should be no need for you to perform commands in your run dialogue.
What is ClickFix?
With this new technical, the attacker creates a false website, or takes over a popular web page and disrupts your web surfing with a fake error message like this one, targeting PC users:
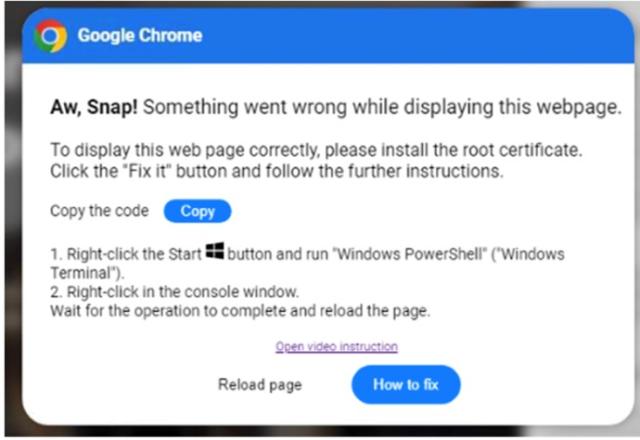
For Mac users, the attack method is the same. In one popular campaign, the user is encouraged to visit a malicious and imposter DeepSeek site. Once the malware is downloaded, the software instructs this user to open the terminal and to drag/drop to install the malware.
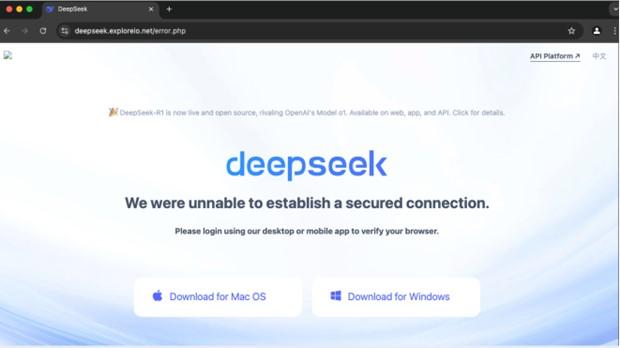
In both cases, what is needed from you, the user, is to go through the extra steps to install the malware, thus bypassing any security measures that protect you.
While these attacks are also being sent to users via email, your security teams are blocking many of these attacks. However, we should all be aware that this activity is occurring, so we can stay vigilant both while interacting with email and conducting normal web browsing at work and at home.
It should also be explicitly stated, given the above example, that you shuld not to enter non-public institutional data into DeepSeek or any other non-university approved AI tools. For updated clarity on that topic, please visit our dedicated web page.